Pentesting vs. DAST vs. ASM: A Guide to Security Testing
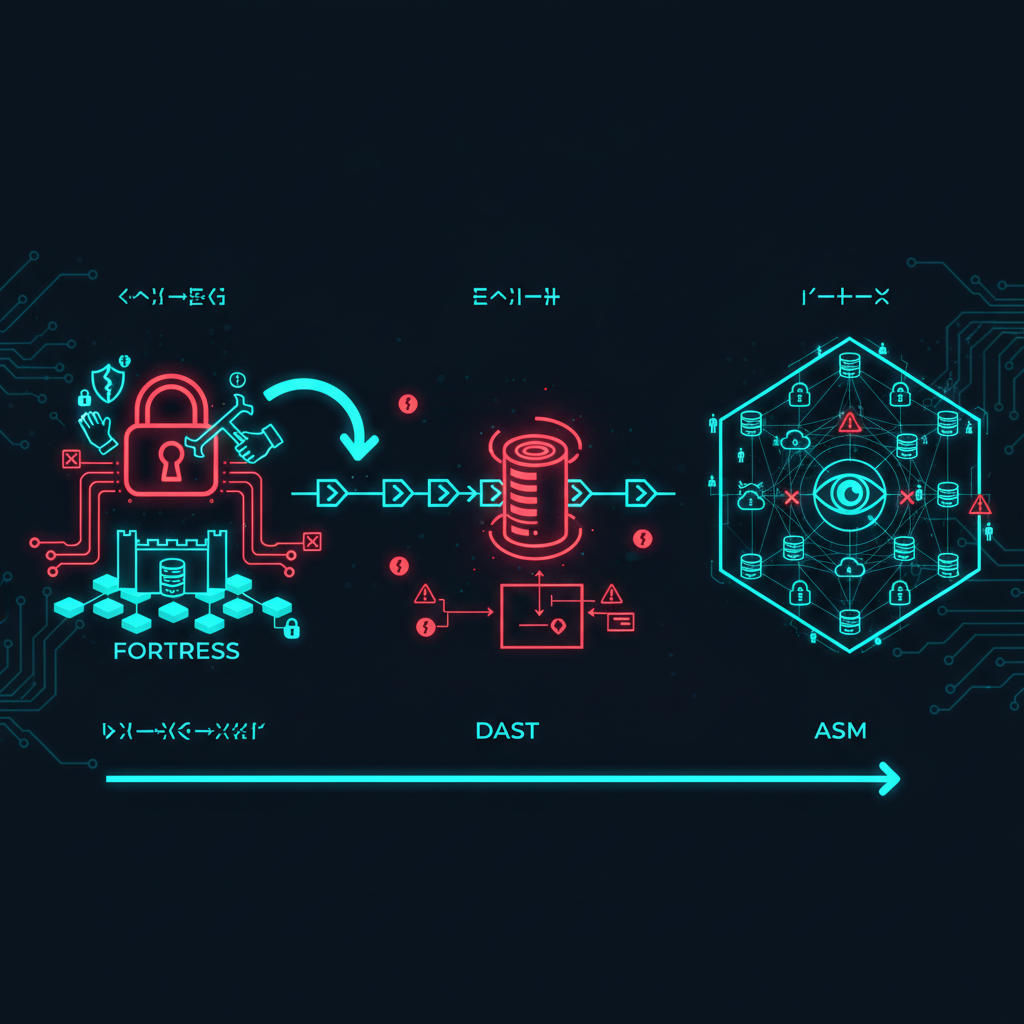
Pentesting, DAST, ASM: The Modern Security Triad
In cybersecurity, ambiguity is the enemy; clarity on your security testing strategy is non-negotiable. Three acronyms dominate the conversation around vulnerability identification: Penetration Testing (Pentesting), Dynamic Application Security Testing (DAST), and Attack Surface Management (ASM). While all three serve the ultimate goal of hardening your defenses, they are not interchangeable. Misunderstanding their distinct roles, scopes, and cadences leads to critical security gaps and wasted resources.
This article dissects the core functions of each methodology, compares their key attributes, and illustrates how to integrate them into a cohesive, modern vulnerability management program that leaves no stone unturned.
Foundational Definitions: What Are We Dealing With?
Before comparing these approaches, we must establish a baseline understanding of what each one is and what it is designed to accomplish.
Penetration Testing (Pentesting): This is a goal-oriented, manual, and human-driven process. Pentesters simulate the actions of a real-world attacker, actively attempting to exploit vulnerabilities and chain them together to achieve a specific objective, such as accessing sensitive data. It’s a deep dive into a predefined scope.
Dynamic Application Security Testing (DAST): DAST is an automated, black-box testing methodology. DAST tools interact with a running application from the outside, just as a user would. They inject malicious payloads and observe the application's responses to identify common security flaws like SQL injection or Cross-Site Scripting (XSS).
Attack Surface Management (ASM): ASM provides continuous, automated discovery and monitoring of an organization's entire external digital footprint. Its primary function is to maintain a comprehensive inventory of all internet-facing assets—known and unknown—and identify associated vulnerabilities, misconfigurations, and exposures.
Key Differentiators: A Comparative Analysis
Understanding the differences in scope, frequency, and output is critical to deploying these tools effectively. The following table breaks down their core distinctions:
| Attribute | Penetration Testing (Pentesting) | Dynamic Application Security Testing (DAST) | Attack Surface Management (ASM) |
|---|---|---|---|
| Scope | Deep, narrow; focused on a specific application, network segment, or objective. | Broad application focus; tests a running application for a wide range of common vulnerabilities. | Comprehensive, wide; discovers and monitors all external assets, including shadow IT and third-party infrastructure. |
| Methodology | Primarily manual; human expertise, creativity, and logic are central to the process. | Fully automated; scans are configured and run without human intervention. | Fully automated and continuous; runs 24/7 in the background to detect changes. |
| Frequency | Infrequent; typically conducted quarterly, semi-annually, or annually due to cost and effort. | High; designed for integration into CI/CD pipelines for frequent, pre-deployment testing. | Continuous; always-on monitoring provides real-time visibility into the attack surface. |
| Ownership | Security Team / Red Team. | Development / DevOps / AppSec Teams. | Security Operations / Vulnerability Management Teams. |
| False Positives | Very low; findings are manually validated and exploited by a human tester. | Can be high; automated tools lack context and cannot always confirm exploitability. | Low; modern ASM platforms include validation steps to confirm vulnerabilities are real and exploitable. |
The Power of Synergy: ASM as the Foundation
Viewing Pentesting, DAST, and ASM as competitors is a strategic error; their true power is unlocked when they are used in concert, with ASM acting as the foundational intelligence layer.
"We used to scope our pentests based on last year's asset list. ASM showed us we were only testing 60% of our actual attack surface. It completely changed the game, allowing our pentesters to focus on the newly discovered, high-risk assets we never knew we had."
- CISO, Financial Services
Here’s how ASM enhances and optimizes your other testing initiatives:
1. Intelligence-Driven Pentest Scoping
An annual pentest scoped on outdated information is a compliance checkbox, not a security assessment. ASM provides a live, comprehensive map of your entire external attack surface. This allows you to:
- Identify High-Value Targets: Direct pentesters toward newly discovered, business-critical applications or infrastructure that may have been deployed outside of normal IT processes.
- Prioritize Weak Points: Use ASM's vulnerability data to focus pentesting efforts on assets with known, critical exposures, maximizing the impact of the engagement.
2. Bridging the Gaps Between Pentests
Your attack surface changes daily; an annual pentest provides a snapshot in time. A new vulnerability or misconfiguration can appear hours after a clean report is delivered. ASM provides the continuous monitoring needed to bridge these gaps, ensuring that emerging threats are identified and remediated long before the next scheduled pentest.
3. Enhancing DAST with Real-World Context
DAST tools are excellent for securing the applications you are building, but they often lack visibility into their production environment and dependencies. ASM provides this context by:
- Mapping the Supply Chain: Identifying third-party services, APIs, and libraries an application relies on, revealing risks that a standard DAST scan would miss.
- Testing Production Parity: Ensuring DAST scans are run against environments that accurately reflect the complexities of the live production infrastructure that ASM has mapped.
Building a Cohesive Security Strategy
An effective, modern security program doesn't choose one approach; it orchestrates all three in a reinforcing loop.
- Start with ASM: Deploy a robust ASM solution to gain continuous, comprehensive visibility over your entire external attack surface. This becomes your single source of truth for what you own and what needs protection.
- Integrate DAST into CI/CD: Shift security left by embedding automated DAST scans into your development pipelines. Catch vulnerabilities early in the lifecycle before they ever reach production.
- Conduct Strategic Pentesting: Use the intelligence gathered from your ASM platform to conduct surgical, objective-driven pentests on your most critical assets. Validate your defenses against a skilled human adversary.
This integrated approach ensures you have broad, continuous coverage from ASM, deep application-level testing from DAST, and expert-led validation from pentesting. It transforms your security testing from a series of disjointed activities into a unified, risk-centric program; this optimizes resources, reduces your mean time to remediation (MTTR), and provides a truly hardened security posture.
END_OF_FILE
HASH: AOYWYGIQSED
Related Intelligence

Flawtrack: Malaysia's Top ASM & CTEM Platform
Discover why Flawtrack, a Malaysian-based cybersecurity firm, surpasses global giants like UpGuard for ASM and CTEM in the Southeast Asian market.
CVE-2025-12420: Critical Flaw in ServiceNow AI
A critical unauthenticated privilege escalation vulnerability (CVSS 9.3) in the ServiceNow AI Platform allows attackers to impersonate users. Patch now.

Brand Protection in Malaysia: MyIPO & SSM Checks
Secure your brand in Malaysia by performing critical trademark (MyIPO) and business (SSM) checks. Learn how to prevent infringement and defend your digital assets.
Ready to Secure Your Infrastructure?
Join forward-thinking engineering teams who trust Flawtrack for continuous vulnerability scanning and threat detection.
Get Started Now