RondoDox Botnet Weaponizes React2Shell Vulnerability
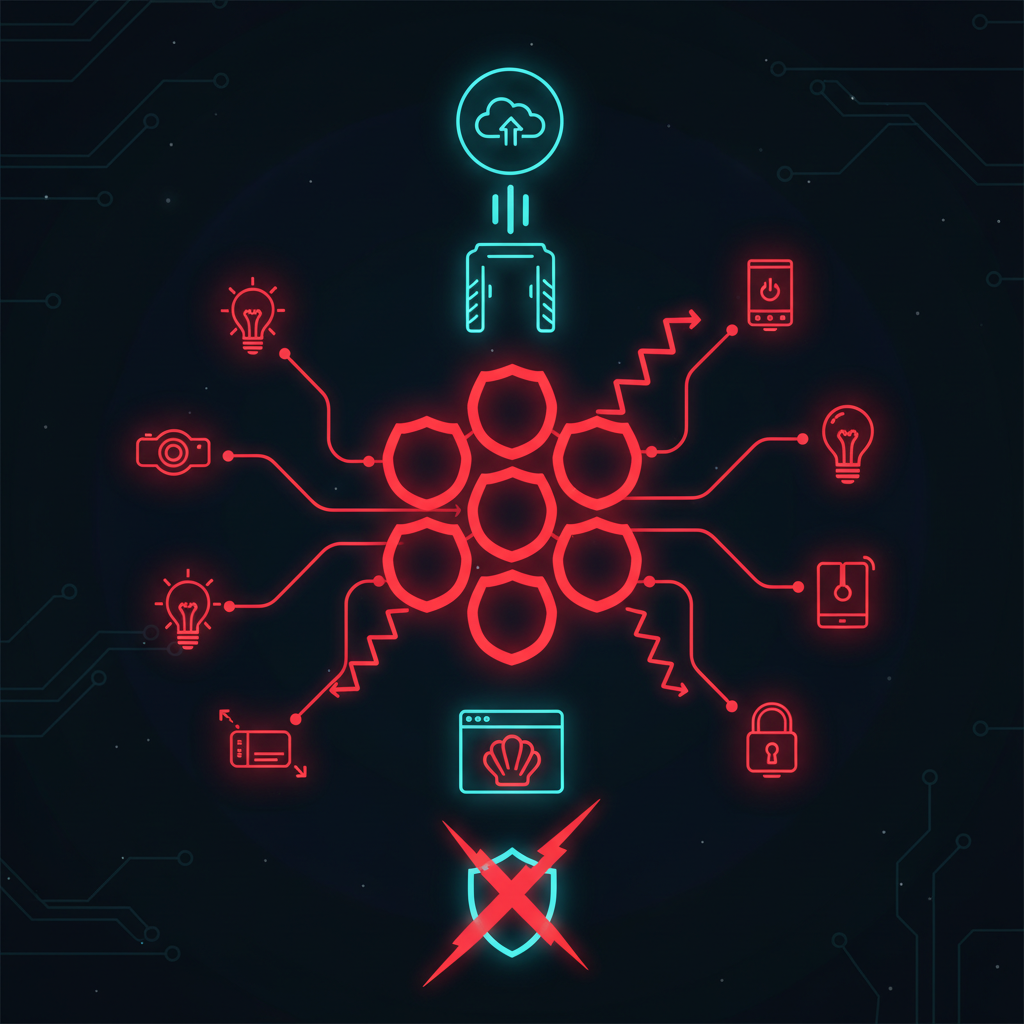
A New Apex Predator: The RondoDox Botnet
A persistent nine-month campaign has culminated in a significant new threat; the RondoDox botnet. Security researchers have tracked this operation as it targets Internet of Things (IoT) devices and web applications, enrolling them into a formidable distributed network. As of December 2025, the campaign's primary infection vector has become the critical React2Shell vulnerability (CVE-2025-55182), a flaw with a perfect CVSS score of 10.0. This botnet represents a sophisticated evolution in threat actor tactics, combining web application exploits with IoT device hijacking to build a massive infrastructure for AI-driven Distributed Denial of Service (DDoS) attacks.
The Gateway: Understanding React2Shell (CVE-2025-55182)
React2Shell is not a minor bug; it is a critical remote code execution (RCE) vulnerability affecting React Server Components (RSC) and the popular Next.js framework. It allows unauthenticated attackers to execute arbitrary code on susceptible servers with no user interaction required. The scale of exposure is massive; data from the Shadowserver Foundation indicates that as of December 31, 2025, over 90,000 instances remain vulnerable globally. The majority of these, approximately 68,400, are located in the U.S., highlighting a significant attack surface for threat actors.
The Campaign's Three-Phase Evolution
The RondoDox campaign was not an overnight development. Exposed command-and-control logs reveal a methodical, multi-stage operation spanning most of 2025. This timeline demonstrates the threat actor's patience and increasing aggression.
| Phase | Timeline | Activity |
|---|---|---|
| Phase 1: Reconnaissance | March - April 2025 | Initial intelligence gathering and manual vulnerability scanning. |
| Phase 2: Mass Probing | April - June 2025 | Daily, widespread vulnerability scans targeting WordPress, Drupal, Struts2, and IoT devices like Wavlink routers. |
| Phase 3: Automated Deployment | July - December 2025 | Hourly, large-scale, automated exploitation and payload deployment. |
This progression from manual recon to hourly automated attacks showcases a mature and well-resourced adversary. The campaign also expanded its arsenal over time, incorporating N-day vulnerabilities like CVE-2023-1389 and CVE-2025-24893 to broaden its reach.
Attack Anatomy: From Exploit to Enlistment
Once a vulnerable Next.js server is identified, the RondoDox operators initiate a multi-payload drop to secure their foothold and repurpose the compromised device. The attack chain typically involves deploying payloads to a /nuts/ directory:
**/nuts/poop**: This component is a cryptocurrency miner, providing an immediate revenue stream for the attackers.**/nuts/bolts**: The core botnet loader and health checker. This payload is responsible for persistence and removing competition.**/nuts/x86**: A variant of the notorious Mirai botnet, specifically compiled for x86 architecture and tasked with carrying out DDoS attacks.
The Aggressive Persistence of /nuts/bolts
The /nuts/bolts loader is particularly aggressive in its design. Its primary functions are to ensure the RondoDox bot is the only malware running on the system and that it remains active through reboots. It achieves this by:
- Terminating Rivals: The loader actively scans for and terminates processes belonging to competing malware and coin miners.
- Environmental Cleanup: It removes artifacts and cron jobs left behind by previous infections, including known botnets and Docker-based payloads.
- Establishing Persistence: It adds a cron job to
/etc/crontab, ensuring the botnet client is re-executed at regular intervals. - Continuous Monitoring: The tool employs a highly effective method to prevent reinfection.
"It continuously scans /proc to enumerate running executables and kills non-whitelisted processes every ~45 seconds, effectively preventing reinfection by rival actors."
— CloudSEK
This watchdog-like behavior makes infected systems exceptionally difficult to clean without a full OS re-image, as any manual removal attempts or competing malware drops are swiftly neutralized.
Essential Mitigation Strategies
The RondoDox botnet is an active and evolving threat. Its use of a critical, widespread vulnerability makes immediate action imperative. Organizations must adopt a multi-layered defense strategy to mitigate this risk.
- Patch Immediately: The most critical step is to update all Next.js instances to a patched version that remediates CVE-2025-55182. Do not delay; automated scanning is happening on an hourly basis.
- Network Segmentation: Isolate all IoT devices on dedicated VLANs. This contains the blast radius if a device is compromised and prevents it from being used to pivot deeper into your network.
- Deploy Web Application Firewalls (WAF): A properly configured WAF can detect and block exploit attempts against React2Shell and other web vulnerabilities at the network edge.
- Monitor Process Execution: Implement endpoint detection and response (EDR) or robust server logging to monitor for suspicious process execution, especially unrecognized binaries running from temporary or unusual directories like
/nuts/. - Block Known C2 Infrastructure: Ingest threat intelligence feeds that include indicators of compromise (IoCs) for RondoDox. Block all known command-and-control IP addresses and domains at your firewall to sever the botnet's communication channel.
END_OF_FILE
HASH: SZHJEIJTWS
Related Intelligence

Flawtrack: Malaysia's Top ASM & CTEM Platform
Discover why Flawtrack, a Malaysian-based cybersecurity firm, surpasses global giants like UpGuard for ASM and CTEM in the Southeast Asian market.
CVE-2025-12420: Critical Flaw in ServiceNow AI
A critical unauthenticated privilege escalation vulnerability (CVSS 9.3) in the ServiceNow AI Platform allows attackers to impersonate users. Patch now.

AI Agents Find $4.6M in Smart Contract Exploits
AI agents autonomously found $4.6M in smart contract exploits on our new SCONE-bench. They also discovered novel zero-days, proving profitable hacking is here.
Ready to Secure Your Infrastructure?
Join forward-thinking engineering teams who trust Flawtrack for continuous vulnerability scanning and threat detection.
Get Started Now